It started with an imprisoned tyrant, a haircut, and a tattooed servant. At least, that's how Herodotus tells it.
Commonly cited as the first example of steganography, concealing a message within another message, an exiled king named Histiaeus wanted to start a revolt against a rival. His solution was to shave and tattoo a message on a servant’s head. When the hair grew back, the hidden message was easily delivered through enemy territory.
Histiaeus performed the first successful steganographic attack. He used data hidden in plain sight to harm a foe. I've always liked this story. It demonstrates how a simple method of hiding data can have disastrous consequences—in this case, a devastating revolt.
Modern steganography-based attacks often hide malware in harmless image files, creating a vital link in the threat actor's infection chain, much like Histiaeus's hidden message was the first link in his attack chain.
Steganography is also used to extract data from victims’ machines. For example, the attacker needs to send data home after accessing a company network. Steganographic-based malware achieves this goal.
How difficult is it to hide malware in images? As a proof-of-concept, it'd be fun to try it and make a video demonstrating my steganographic image attack journey. Thankfully, no scalp tattooing is required!
How Easy is it to Create Image Steganography Malware?
These attacks may seem sophisticated, but software makes embedding data into images painless. Free and available steganography programs like 1-2 Steganography, OpenStego, and QuickStego are readily available and user-friendly.
With these tools, malware can be created and extracted in a few minutes with a few lines of code. The code pictured below demonstrates how I used the judyb Python library to hide and reveal data in images.
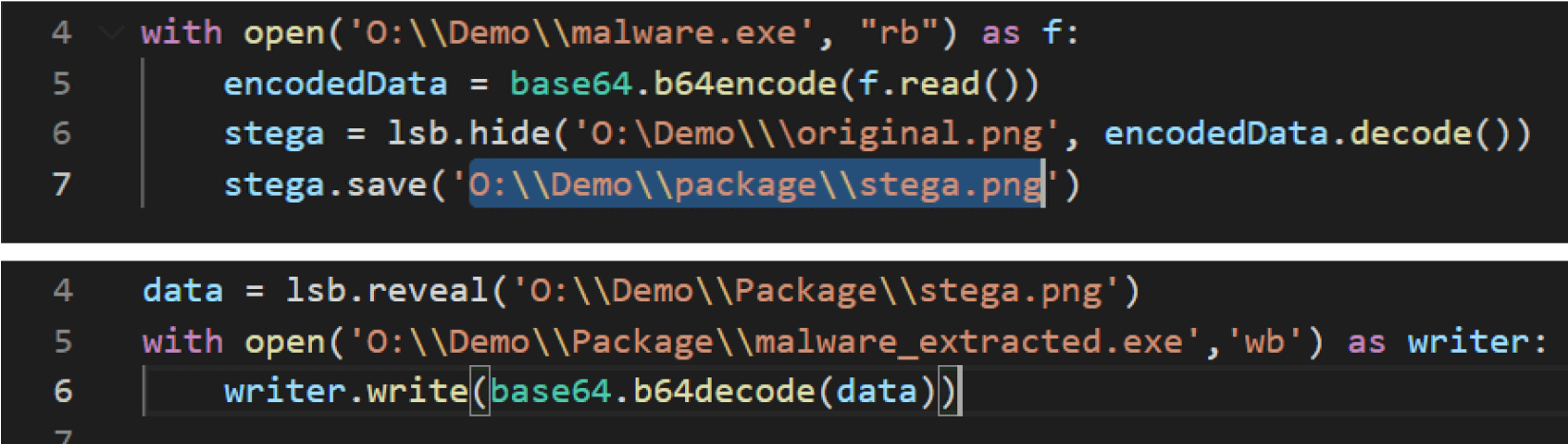
With a simple Python module, you, too, can hide information in images and send it anywhere you want. Steganography is fun. You can use it to pass secret messages to friends, but attackers can spread malware and infect networks.
Why is it efficient?
It's easy to hide malware in images but challenging to detect.
Attackers embed data at the bit/pixel level, so a malicious payload is nearly impossible to detect with most anti-malware scanning tools. Harmful images easily bypass most real-time anti-malware detection methods.
How to Prevent Stenographic Attacks – Deep Content Disarm & Reconstruction
Since detection-based methods are ineffective, we need another way to detect malicious code hidden in images.
Fortunately, there is a powerful method called CDR (Content Disarm and Reconstruction) for breaking down files to remove harmful data. Also known as data sanitization, CDR is a zero-trust security solution that assumes all files are malicious. It deconstructs files and removes executable content and elements that do not match the file type standards inside the files. Lastly, it reconstructs the files ensuring full usability with safe content.
A more powerful version of CDR called Deep CDR, further inspects images by looking at profiles, metadata, and pixels for harmful content.
Deep CDR uses recursive sanitization to neutralize threats. If the attacker embedded this image in a PDF, Deep CDR scans and sanitizes every object in the PDF.
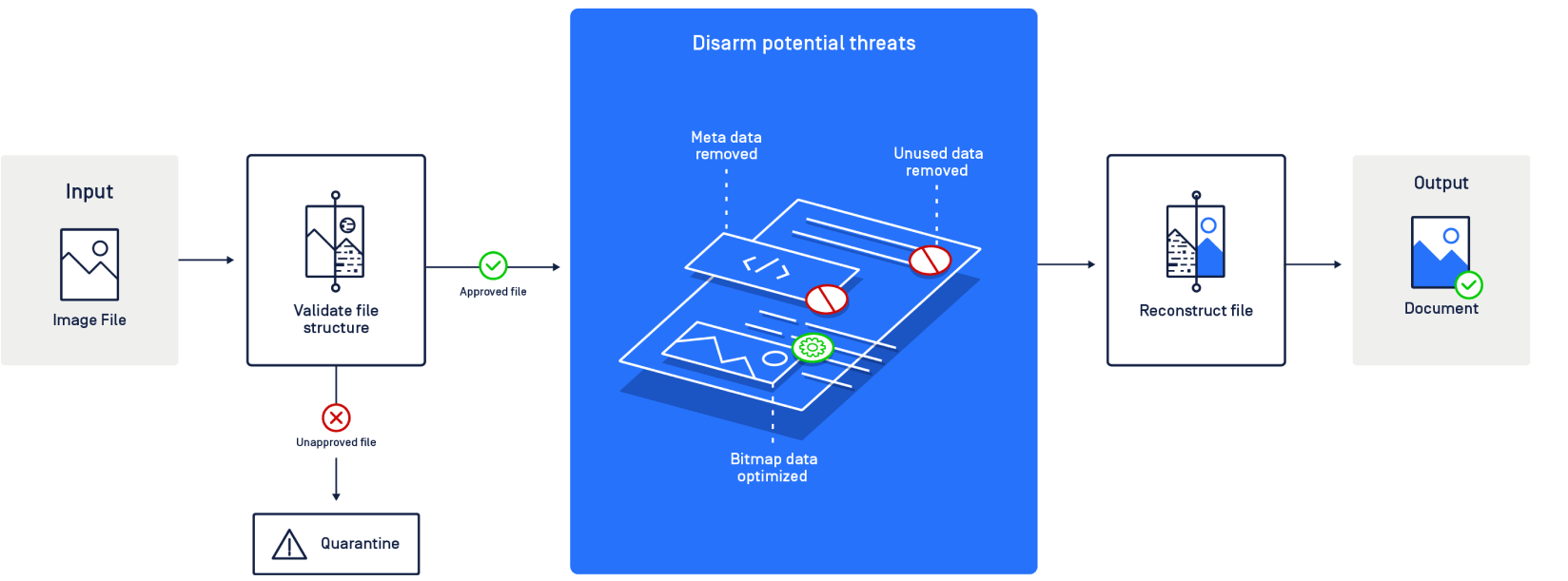
It also removes any structured metadata, which helps with privacy and security. Attackers can hide trojans in metadata. Stripping the metadata from the image file prevents this attack vector.
At the pixel level, our program removes unused data which potentially contains the partial payload. It adds random noise to those pixels, which disrupts the payload's ability to execute the harmful code.
We can also optimize the bitmaps data. The compression algorithm removes unused data where the malicious data is hidden without affecting the quality of images.
As you can see in the example below, the image quality remains the same.
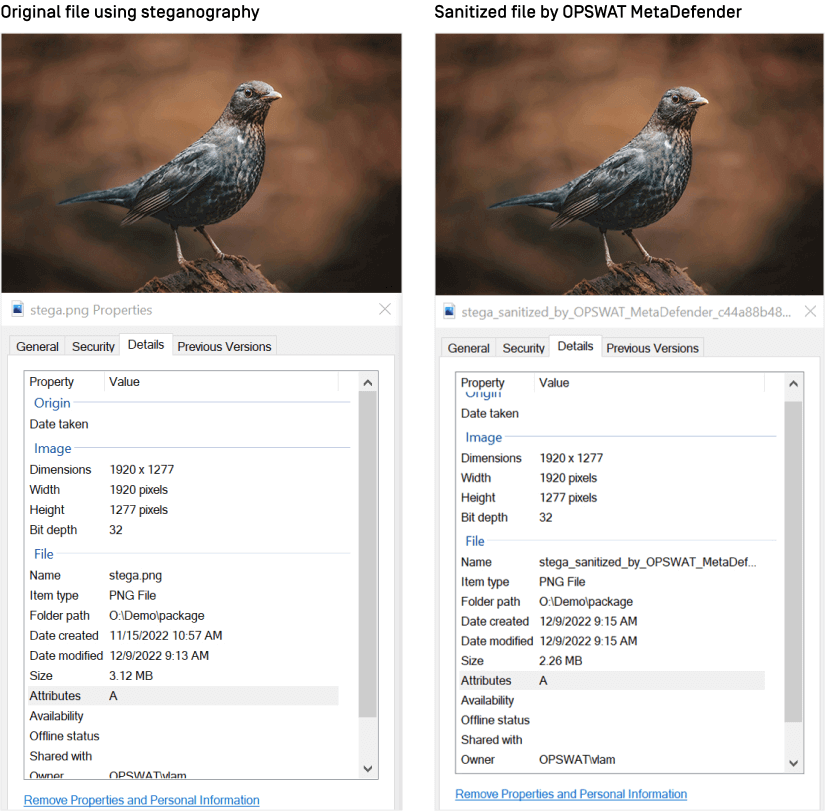
If you like learning about steganography and are interested in more cybersecurity topics, sign up for our mailing list.
Worried about your organization's cybersecurity? Contact an OPSWAT security expert today!

